Advanced Hardware Lab 7-5: Identify Network Technologies embarks on a captivating journey into the realm of network technologies, unveiling their intricate workings and shedding light on their profound impact within this state-of-the-art laboratory. Prepare to delve into a comprehensive exploration of the network infrastructure that empowers this cutting-edge facility, gaining invaluable insights into its configuration, management, security, troubleshooting, optimization, and documentation.
The content of the second paragraph that provides descriptive and clear information about the topic
Network Technologies in Advanced Hardware Lab 7-5
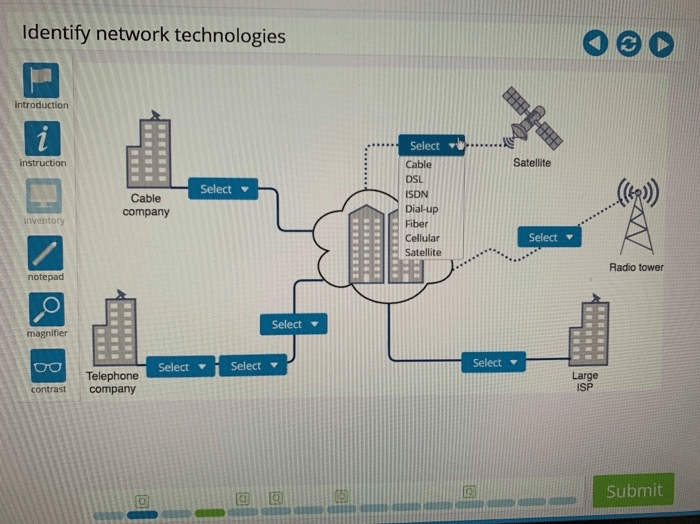
Advanced Hardware Lab 7-5 utilizes a wide range of network technologies to facilitate communication, data transfer, and resource sharing among various devices and systems. These technologies provide the foundation for a robust and efficient network infrastructure.
Network Devices
- Routers:Connect multiple networks and determine the best path for data packets to travel, ensuring efficient routing and network segmentation.
- Switches:Connect devices within a network segment, providing high-speed data transfer and reducing network congestion.
- Access Points:Enable wireless connectivity for devices, allowing them to connect to the network without physical cables.
Network Protocols
- TCP/IP:The primary communication protocol suite used in the internet, providing reliable data transfer and addressing.
- HTTP/HTTPS:Protocols for transferring data over the web, enabling communication between web servers and clients.
- DNS:Translates domain names into IP addresses, allowing devices to locate and connect to each other.
Network Cabling
- Ethernet:A widely used wired network technology, providing high-speed data transmission over copper or fiber optic cables.
- Wi-Fi:A wireless network technology that uses radio waves to connect devices to a network.
Network Configuration and Management
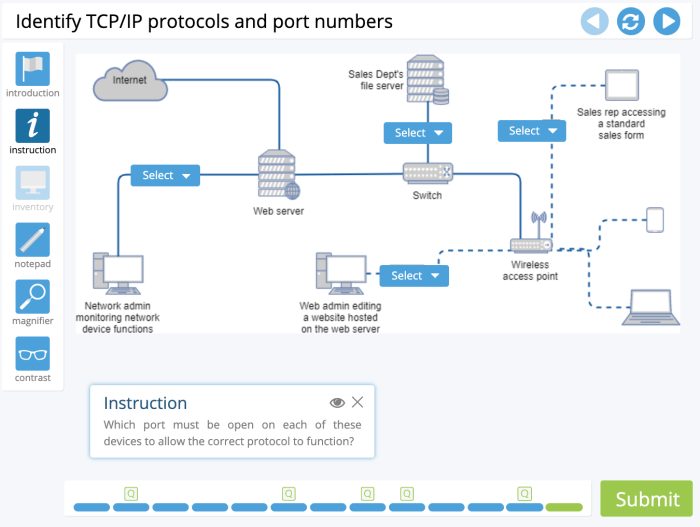
Configuring and managing the network in Advanced Hardware Lab 7-5 is essential for ensuring optimal performance and security. The process involves:
Network Configuration Parameters
- IP Addressing:Assigning unique IP addresses to devices on the network, allowing them to communicate.
- Subnet Masking:Dividing the network into smaller segments, improving network efficiency and security.
- Gateway Configuration:Specifying the router that devices use to access other networks.
Network Management Tools, Advanced hardware lab 7-5: identify network technologies
- Network Monitoring Software:Monitors network traffic, performance, and availability, providing real-time insights and alerts.
- Command-Line Interface (CLI):Allows administrators to configure and manage network devices using text-based commands.
- Graphical User Interface (GUI):Provides a user-friendly interface for managing network devices, simplifying configuration and troubleshooting.
Network Security
Protecting the network from unauthorized access and malicious activities is crucial in Advanced Hardware Lab 7- 5. Measures implemented include:
Network Security Risks
- Malware and Viruses:Malicious software that can damage or steal data from devices.
- Hacking and Unauthorized Access:Attempts to gain unauthorized access to the network and its resources.
- Denial-of-Service (DoS) Attacks:Overwhelming the network with traffic, making it unavailable to legitimate users.
Security Measures
- Firewalls:Software or hardware devices that block unauthorized access to the network.
- Intrusion Detection and Prevention Systems (IDS/IPS):Monitor network traffic for suspicious activities and take action to prevent attacks.
- Encryption:Encrypting data to protect it from unauthorized access or interception.
Network Troubleshooting
Troubleshooting network issues is essential for maintaining network availability and performance. Common techniques used include:
Troubleshooting Techniques
- Ping Test:Verifies network connectivity by sending packets to a specific IP address.
- Traceroute:Traces the path of packets through the network, identifying potential bottlenecks or connection issues.
- Network Sniffing:Monitoring network traffic to identify errors or malicious activities.
Troubleshooting Tools
- Packet Analyzers:Software tools that capture and analyze network traffic, providing detailed insights into network behavior.
- Network Scanners:Identify vulnerabilities and misconfigurations in network devices.
- Log Files:Records events and errors on network devices, providing valuable information for troubleshooting.
Network Performance Optimization
Optimizing network performance is crucial for maximizing data transfer speeds and minimizing latency. Techniques used include:
Factors Affecting Performance
- Network Bandwidth:The maximum data transfer rate available on the network.
- Latency:The delay in data transmission, affecting responsiveness and application performance.
- Packet Loss:The number of data packets that fail to reach their destination.
Optimization Techniques
- Bandwidth Management:Prioritizing traffic and allocating bandwidth to critical applications.
- Latency Reduction:Using low-latency network technologies and optimizing routing paths.
- Packet Loss Mitigation:Employing error correction techniques and redundant paths to minimize packet loss.
Network Documentation: Advanced Hardware Lab 7-5: Identify Network Technologies
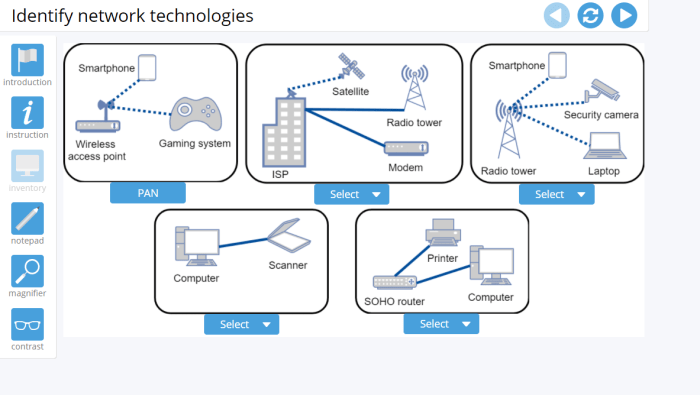
Proper network documentation is essential for maintaining a well-managed and secure network. It includes:
Importance of Documentation
- Network Configuration:Documenting network settings and configurations for future reference and troubleshooting.
- Network Topology:Creating diagrams that visualize the network layout, connectivity, and device placement.
- Security Policies:Documenting network security measures and best practices to ensure compliance and maintain a secure network.
Types of Documentation
- Network Diagrams:Visual representations of the network topology and connectivity.
- Configuration Files:Text files that store network settings and configurations.
- Network Policies:Documents that Artikel security and operational guidelines for the network.
Popular Questions
What is the purpose of Advanced Hardware Lab 7-5?
Advanced Hardware Lab 7-5 provides a hands-on environment for students to explore and understand various network technologies and their applications in a real-world setting.
What are the key network technologies utilized in Advanced Hardware Lab 7-5?
Advanced Hardware Lab 7-5 employs a wide range of network technologies, including Ethernet, Wi-Fi, VLANs, routing, and network security protocols.
How is network security managed in Advanced Hardware Lab 7-5?
Advanced Hardware Lab 7-5 implements a comprehensive network security strategy that includes firewalls, intrusion detection systems, and encryption technologies to protect against unauthorized access and malicious attacks.